The massive “Salt Typhoon” cyberattack has infiltrated at least 200 American organizations and hundreds more around the world, and a joint international advisory this month identified three Chinese companies it said were linked to it.
The three firms—Sichuan Juxinhe Network Technology, Beijing Huanyu Tianqiong Information Technology, and Sichuan Zhixin Ruijie Network Technology—“provide cyber-related products and services to China’s intelligence services, including multiple units of the People’s Liberation Army and the Ministry of State Security,” said the advisory, which was issued by the U.S. and 12 other nations.
But it offered no further information about how the three Chinese companies operate, or why they were positioned to play such a central alleged role in the Salt Typhoon attack. While the Treasury Department had sanctioned Sichuan Juxinhe in January, the advisory was the first time the other two had been publicly named in connection with global hacking operations.
A Kharon review of government notices, bidding documents and corporate records found that one company has received years of state backing. Leadership and location connect more dots between the three—and to China’s broader cybersecurity apparatus.
According to the FBI, the campaign has impacted at least 600 companies in all across at least 80 countries, making it one of the largest espionage operations linked to China in recent years.
The designation: In sanctioning Sichuan Juxinhe earlier this year, the Treasury Department said the cybersecurity company had “direct involvement” in the Salt Typhoon cyber group and “strong ties” to China’s Ministry of State Security. Treasury said the MSS had maintained such ties with “other computer network exploitation companies” as well.
What it’s said: A 2022 job posting summed up Sichuan Zhixin Ruijie’s government-oriented business, describing the company as “rapidly growing, primarily serving government and military sectors, and providing customized heavyweight big data information.”
Meanwhile, the Salt Typhoon attack had begun.
According to corporate records, Yu Yang served as legal representative and the person in charge at Beijing Huanyu Tianqiong until December 2021. He then became the controlling shareholder at Sichuan Zhixin Ruijie, with a 50% stake and a supervisor position.
The three firms—Sichuan Juxinhe Network Technology, Beijing Huanyu Tianqiong Information Technology, and Sichuan Zhixin Ruijie Network Technology—“provide cyber-related products and services to China’s intelligence services, including multiple units of the People’s Liberation Army and the Ministry of State Security,” said the advisory, which was issued by the U.S. and 12 other nations.
But it offered no further information about how the three Chinese companies operate, or why they were positioned to play such a central alleged role in the Salt Typhoon attack. While the Treasury Department had sanctioned Sichuan Juxinhe in January, the advisory was the first time the other two had been publicly named in connection with global hacking operations.
A Kharon review of government notices, bidding documents and corporate records found that one company has received years of state backing. Leadership and location connect more dots between the three—and to China’s broader cybersecurity apparatus.
The Background
The Salt Typhoon attack has been active since “at least 2021,” targeting foreign telecommunications and internet service providers as well as networks in the hospitality and transportation industries, the advisory said. The operation, it said, “ultimately can provide Chinese intelligence services with the capability to identify and track their targets’ communications and movements around the world.”According to the FBI, the campaign has impacted at least 600 companies in all across at least 80 countries, making it one of the largest espionage operations linked to China in recent years.
The designation: In sanctioning Sichuan Juxinhe earlier this year, the Treasury Department said the cybersecurity company had “direct involvement” in the Salt Typhoon cyber group and “strong ties” to China’s Ministry of State Security. Treasury said the MSS had maintained such ties with “other computer network exploitation companies” as well.
Government-Backed Growth
Sichuan Zhixin Ruijie, based in Sichuan Province’s capital of Chengdu, was founded in 2018. It soon thereafter began seeking recognition from local authorities through state-backed programs, documents reviewed by Kharon show, and it steadily built government connections in the years before this month’s advisory connected it to Salt Typhoon.- In 2021, Sichuan Zhixin Ruijie had earned a place on Chengdu’s “Cultivated List” for small and medium-sized enterprises, a designation that confers access to grants, tax incentives and government contracts. The city government’s goal, it wrote in a notice, was to cultivate the selected companies into “specialized and innovative” firms and “hidden champions.”
- In the end of 2022, the Sichuan Provincial Department of Science and Technology recognized Sichuan Zhixin Ruijie as a “high-tech enterprise.” That status entitled it to “enjoy a series of policy preferences and support, including tax exemptions, financial subsidies, project support, talent introduction,” according to a government announcement.
- By 2024, Sichuan Zhixin Ruijie had been recognized on a provincial-level “List of Innovative Small and Medium-Sized Enterprises,” qualifying it for further state support.
What it’s said: A 2022 job posting summed up Sichuan Zhixin Ruijie’s government-oriented business, describing the company as “rapidly growing, primarily serving government and military sectors, and providing customized heavyweight big data information.”
Meanwhile, the Salt Typhoon attack had begun.
Leadership Connections
Key personnel connect Sichuan Zhixin Ruijie and Beijing Huanyu Tianqiong, the other newly accused Chinese company.According to corporate records, Yu Yang served as legal representative and the person in charge at Beijing Huanyu Tianqiong until December 2021. He then became the controlling shareholder at Sichuan Zhixin Ruijie, with a 50% stake and a supervisor position.
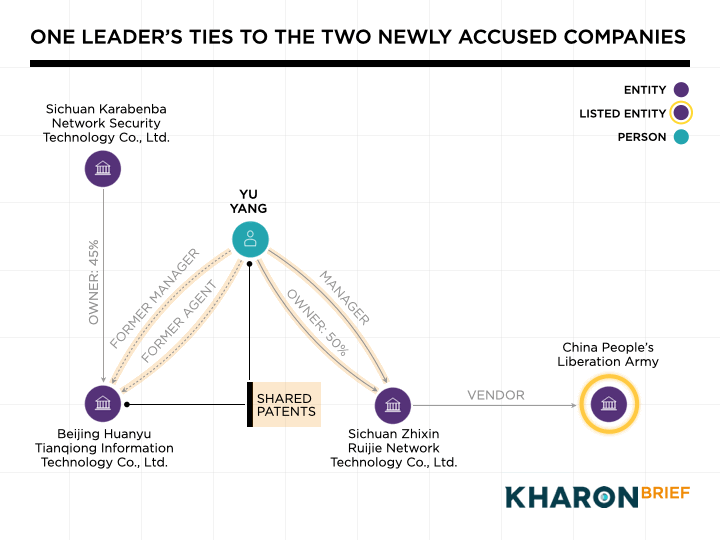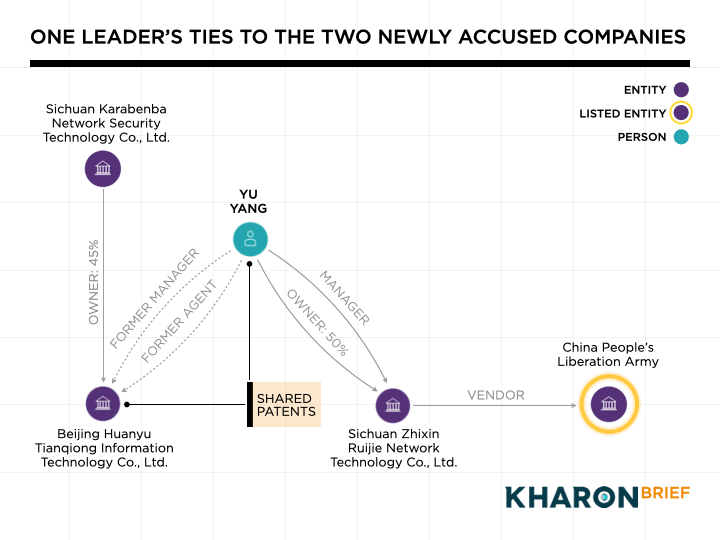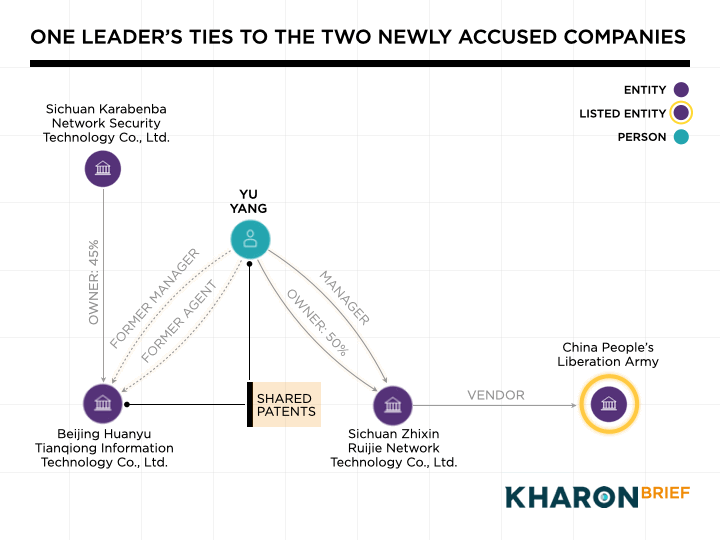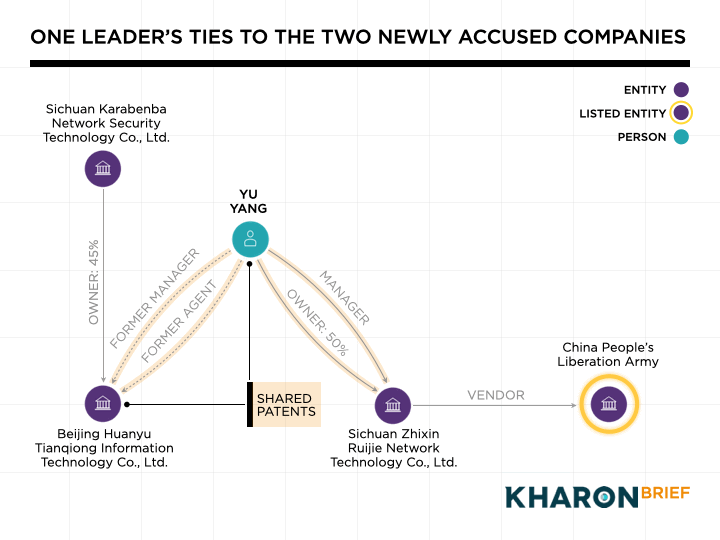
Between 2022 and 2024, after he’d left Beijing Huanyu Tianqiong, Yu was listed as a co-inventor on three cybersecurity-related patents that his old company filed, alongside its founder, Shang Xuejing.
The Sichuan Hub
Sichuan Province, where two of the companies are located, along with Beijing Huanyu Tianqiong Information Technology’s largest (45%) shareholder, has emerged in recent years as a national hub for state-backed cybersecurity firms. It reflects China’s systematic approach to building its cyber capabilities.- The province received a significant boost in 2019, when it was designated as a “National Digital Economy Innovation and Development Pilot Zone.” That came with funding and policy guidance from the National Development and Reform Commission and the Cyberspace Administration of China, two of the country's most powerful central agencies.
- Local officials have set a target of making the digital economy more than 40% of Sichuan’s GDP. Central to this strategy are the cybersecurity industry, which ranks second nationwide, and military electronic equipment, which ranks first.

China announced the National Digital Economy Innovation and Development Pilot Zone in October 2019. Sichuan was among the six provinces and cities selected. (Sichuan government)
The impact is already visible. A recent high-profile case demonstrates the province’s growing role in China’s cyber apparatus.
The details: Last December, the United States charged and sanctioned Guan Tianfeng, a Chinese hacker based in Sichuan, “for his involvement in a conspiracy to hack indiscriminately into firewall devices worldwide in 2020.”
The State Department posted a bounty of up to $10 million for information on him or his employer, Sichuan Silence Technology, which the U.S. also sanctioned. Treasury said that many of the cyberhack victims were “U.S. critical infrastructure companies.”
And earlier this week, in his first public appearance since his appointment, National Cyber Director Sean Cairncross called for a “whole of nation” effort to deter nation-state hackers. He named Salt Typhoon as one of the “most egregious examples of China’s audacity.”
“We must work together,” Cairncross said, “using all of our nation’s cyber capabilities, to shape adversary behavior and, most importantly, shift the burden of risk in cyberspace from Americans to them. That’s what my team and I are here to do.”
More from the Kharon Brief:
The details: Last December, the United States charged and sanctioned Guan Tianfeng, a Chinese hacker based in Sichuan, “for his involvement in a conspiracy to hack indiscriminately into firewall devices worldwide in 2020.”
The State Department posted a bounty of up to $10 million for information on him or his employer, Sichuan Silence Technology, which the U.S. also sanctioned. Treasury said that many of the cyberhack victims were “U.S. critical infrastructure companies.”
Looking Ahead
The U.S. government has continued to call out Chinese cyber threats as a focal point for enforcement efforts since. In March’s Annual Threat Assessment, the Office of the Director of National Intelligence wrote that China represents “the most active and persistent cyber threat” to the United States.And earlier this week, in his first public appearance since his appointment, National Cyber Director Sean Cairncross called for a “whole of nation” effort to deter nation-state hackers. He named Salt Typhoon as one of the “most egregious examples of China’s audacity.”
“We must work together,” Cairncross said, “using all of our nation’s cyber capabilities, to shape adversary behavior and, most importantly, shift the burden of risk in cyberspace from Americans to them. That’s what my team and I are here to do.”
More from the Kharon Brief: